Nmap scan:
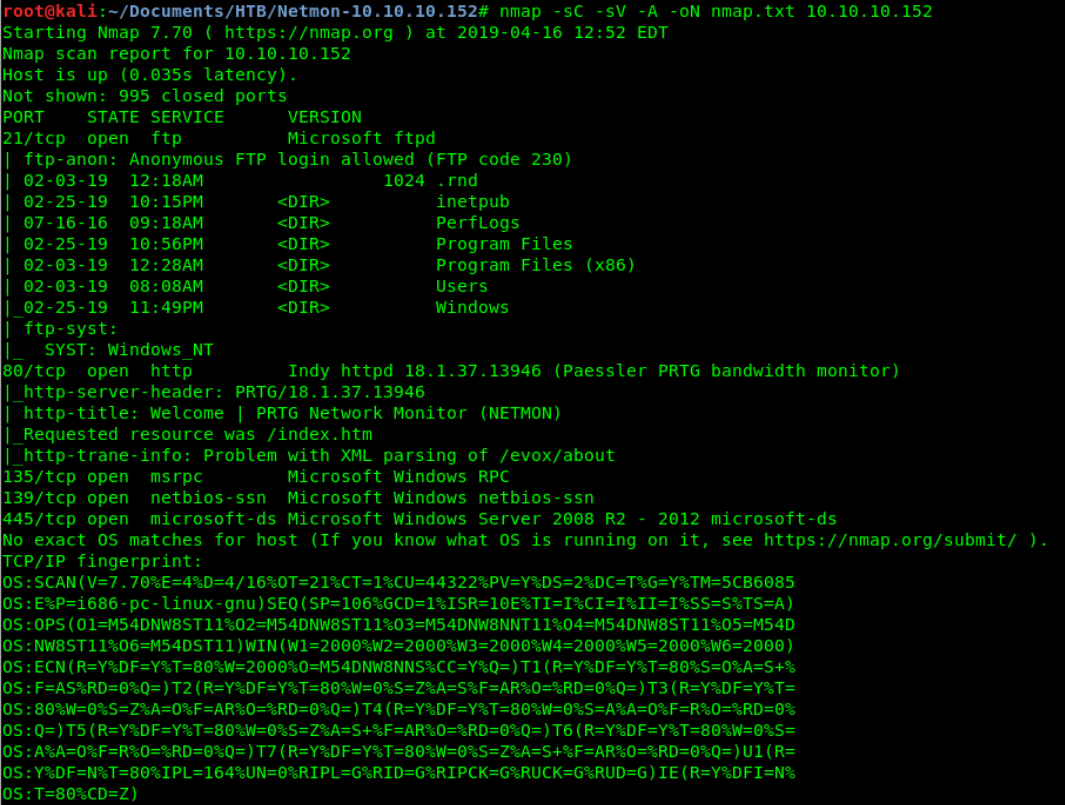
First observation: ftp – anonymous login allowed
PRTG 18.1.37
Let’s try ftp anonymous login:
Basic shell – nice!
Let’s cd around
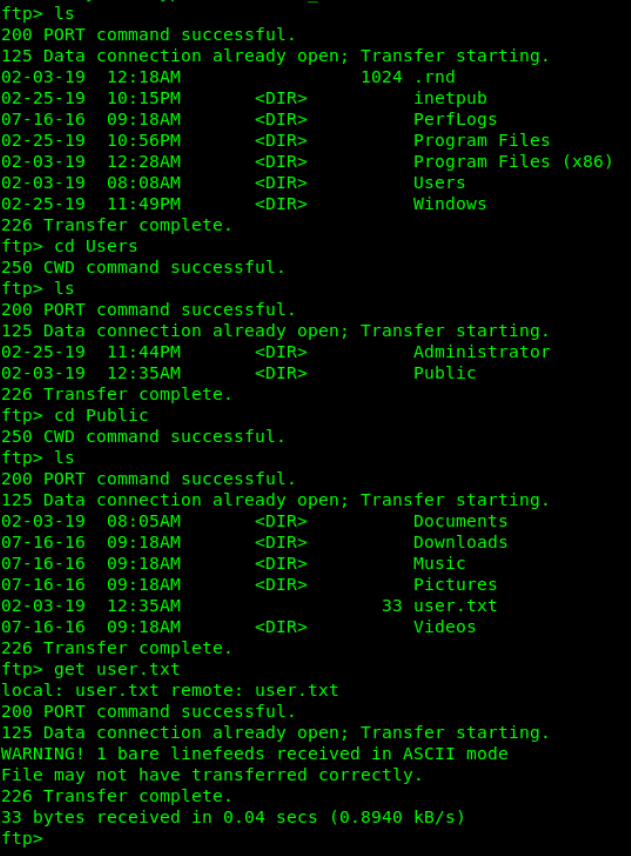
Holy shit that was easy!
Now onto root:
PRTG 18.1.37 -> known vulnerability ->
https://kb.paessler.com/en/topic/463-how-and-where-does-prtg-store-its-data
So the app stored away some plaintext passwords in backup files.
Let’s search them
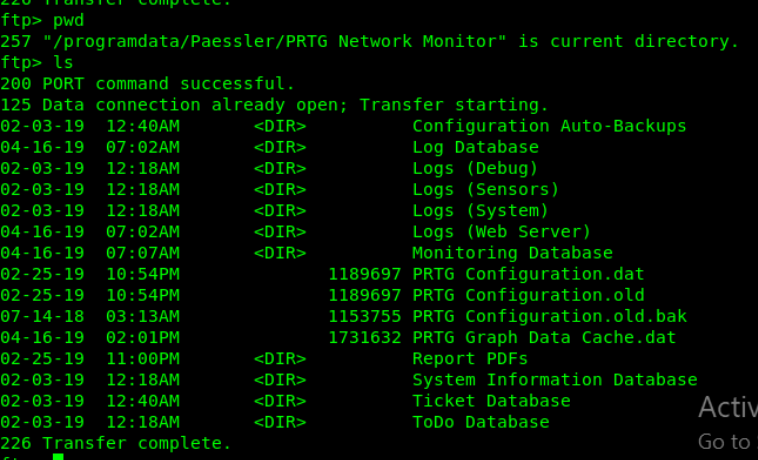
Get 3 config files and look in all of them for plaintext passwords
Hint: put .txt behind it and open with leafpad
Search on password
.old.bak had this
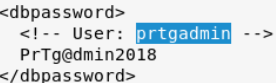
Failed…
Going through the forumsomeone said “what year are we in rn?”
Trying 2019…
Prtg 18.1.37 rce exploit
https://github.com/M4LV0/PRTG-Network-Monitor-RCE
Use burp to capture cookie
Feed it to exploit
Now we created a user. Time to connect to it.
https://github.com/SecureAuthCorp/impacket
Got root shell!!!
Root flag check
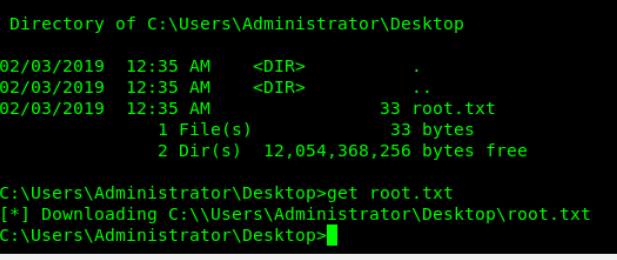
3018977fb944bf1878f75b879fba67cc –> root flag is password want box is nog active (verwijder deze regel maar in write up)
